Estimated reading time: 4 minutes
Table of contents
Executive Summary
Jarrett | Hoyt are Attorneys located at 1795 Williston Rd in South Burlington, Vt in the KeyBank Building near Burlington International Airport. Provided is an overview for an Implementation of Phishing Resistant MFA [Multi Factor Authentication] and Passwordless Authentication.
Implementation
Contact Us if we can help your Implementation of Conditional Access.
Passwordless Authentication
Device Registration
The Employee has been provided a Hardware Identity Device like a Yubikey 5c for Access to Company Resources and performs a Device Registration at URL My Sign-Ins (microsoft.com) as shown below:

Company Portal
This Article describes an implementation of the Yubikey 5 Hardware Device. We use the Yubikey 5C’s in our Azure Conditional Access Policies for the Login Sequence. Passwordless Authentication for a mature Employee Experience by reducing repetitive tasks.
The Security Team purchased the YubiKey and set out to implement the Devices in day-to-day operations. This Blog Post is to aid our Security Team in Learning about the Rollout. Hopefully this Post will help anyone else implementing Phishing Resistant MFA in Azure with Conditional Access.
We share a Workflow for Microsoft Azure Conditional Login for Employee Access to Company Services via Company Portal.

Conditional Access
Conditional Access for Passwordless Authentication when using Hardware Devices like the Yubikey offer the opportunity for Tenant Lockout. Step 1 was to skip the Report-only Option for Conditional Access and Turn On. A live configuration for Azure Conditional Access with Phishing Resistant MFA for Production is shown below.

Passwordless Authentication
Configuration
Policy Example
This is an Example Conditional Login Policy for Phishing Resistant MFA for Azure. The Screen Grab is a starting point for a live Conditional Access Policy as shown below:

Phishing Resistant MFA Login Step 1
The Login Sequence begins just like any other Login Attempt with the User being Presented with a Credential Screen as shown below to Enter the Hardware PIN in Step 1:
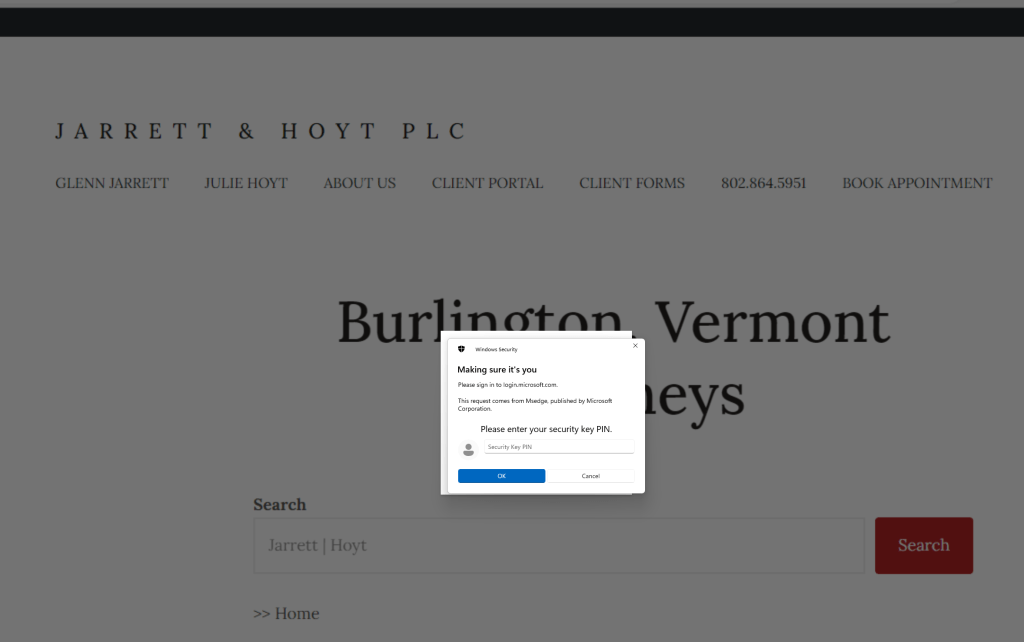
Passwordless Authentication Login Step 2
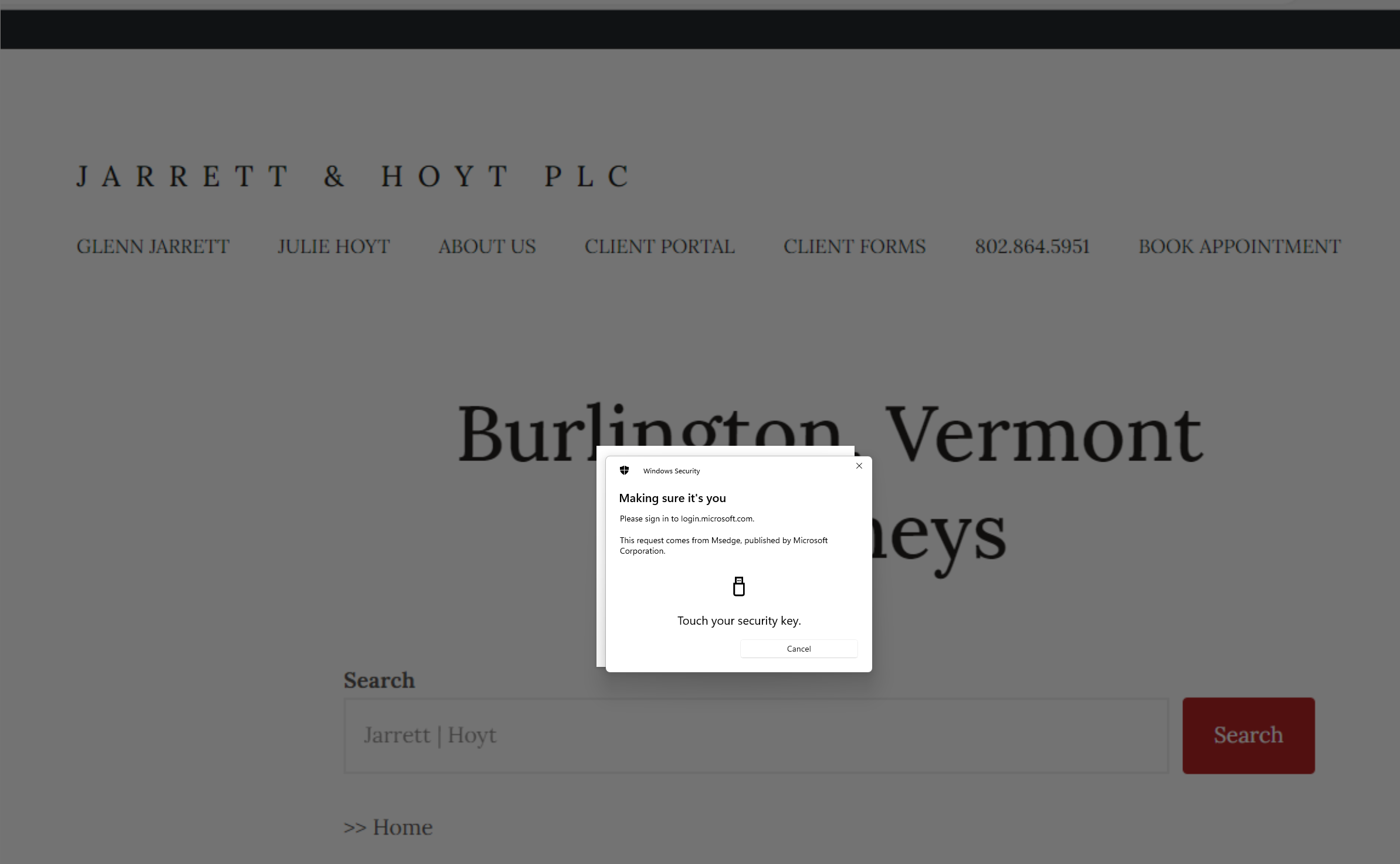
The Login Sequence the Challenges the Login Attempt with the User being Presented with a Credential Screen as shown below to Touch your Key in Step 2:

Activity Details
The Activity Details portion of the Sign-in Log provides the Confirmation that the Phishing Resistant MFA Conditional Access Policy is Enforced as shown below:

Conclusion
Implementing the Conditional Access Policy for the Phishing Resistant MFA Yubikey 5C took less than 15 minutes and resulting in reducing the number of password requests, a better work experience with additional security.
You must be logged in to post a comment.